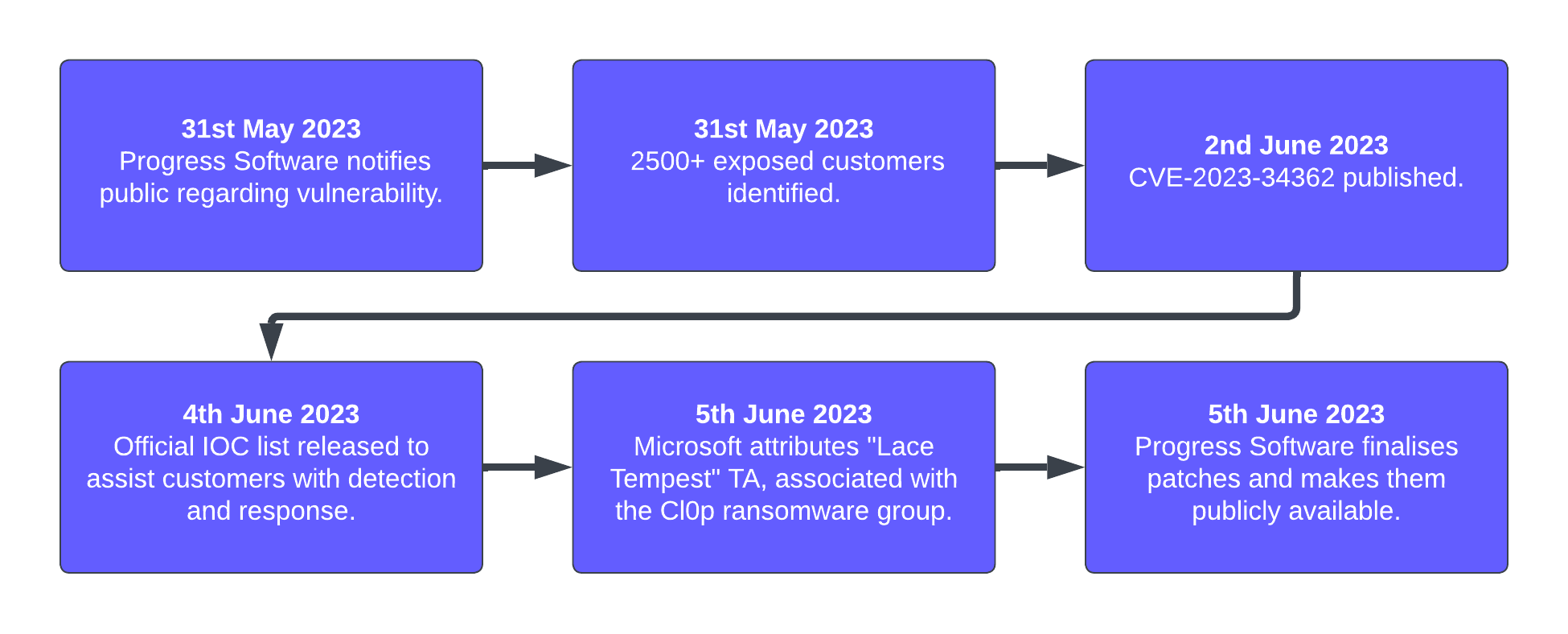
On May 31, 2023, Progress Software warned the public about a critical SQL injection vulnerability in MOVEit Transfer, allowing unauthorised access to its database. Identified as CVE-2023-34362 on June 2, this flaw was exploited four days before the alert.
As of May 31, around 2,500 MOVEit instances, primarily in the US, were exposed online; however, a number of UK-based organisations are also known to be affected, including the BBC, British Airways and Boots.
These types of vulnerabilities offer not just the dumping of confidential data, but initial access to corporate networks, which is being actively exploited by ransomware groups. By June 5, Microsoft tied the attacks to the Lace Tempest Threat Actor (TA), a group associated with Cl0p ransomware and extortion. Organisations may also be indirectly affected as a result of data transfer with third parties using MOVEit Transfer.
Progress Software highly recommends that customers review all activity over the past 30 days for potential breaches.
Remediation
CVE-2023-34362 affects all MOVEit Transfer versions released before May 31, 2023. Patches are available for these versions, and due to the critical nature of this vulnerability, we recommend applying them immediately. In a recent update, Progress Software emphasised the importance of downloading patches exclusively from their official knowledge base articles to avoid potential security risks from third-party sources.
Furthermore, MOVEit Cloud, another product in the MOVEit suite, has also been impacted by this vulnerability. Progress Software confirmed that global patches were completed by June 5th. For MOVEit Transfer users who integrate with Microsoft Azure, it is strongly advised to rotate their Azure storage keys to ensure the security of their data.
MOVEit Transfer users are advised to establish firewall rules blocking both HTTP and HTTPS traffic on ports 80 and 443 until patches are installed. Furthermore, any unauthorized files or user accounts, such as “.cmdline” scripts or “human2.aspx” instances, should be promptly removed.
CISA and Redcentric both urge that MOVEit Transfer customers read the following advisory produced by Progress Software.
Identifying Compromise
MOVEit writes its own Windows EVTX file, which is located at C:\Windows\System32\winevt\Logs\MOVEit.evtx. The MOVEit event logs contain a single event ID (Event ID 0) that provides a plethora of information, including the following:
- File name
- File path
- File size
- IP address
- Username that performed download
Affected organisations and incident responders can use this information to identify which data and how much was exfiltrated, which may also aid in meeting regulatory compliance standards where applicable. It is critical that MOVEit customers capture this log data before wiping or restoring the application from an earlier backup.
Event logging is not enabled by default in MOVEit Transfer, and therefore this information may not be available.
How can we help?
Redcentric can provide assistance to:
- Identify signs of prior exploitation and data theft.
- Oversee remediation activity and validate that any remediations are effective.
We can help. Reach out to our cyber security team at Redcentric if you believe you may be affected by the vulnerability and require any support.