For businesses moving their systems to the cloud, they need to overcome one major challenge: securing them in their new environment.
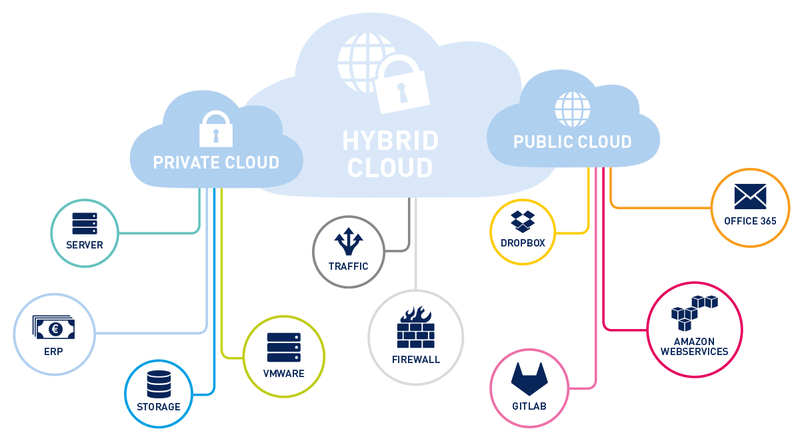
The merging of public and private clouds into a hybrid cloud presents challenges like securing your supply chain, protecting data and complying with regulations. Gartner Research shows that by the end of 2020, 90% of organisations will have moved to a hybrid cloud system, which is why it’s so important that we know how to make (and keep) those systems secure.
Gartner research director DD Mishra says while organisations adopt hybrid infrastructure to optimise costs and increase efficiency, it’s not a straightforward move:
“It increases the complexity of selecting the right toolset to deliver end-to-end services in a multi-sourced environment,” she says.
The good news is that there are ways to secure your hybrid cloud and best practices you can follow to make the adoption of this technology a success. In this piece, we’re going to break down:
- What is hybrid cloud security?
- The main security issues in hybrid cloud computing
- How to secure hybrid cloud
- 3 hybrid cloud security best practices
Let’s get started.
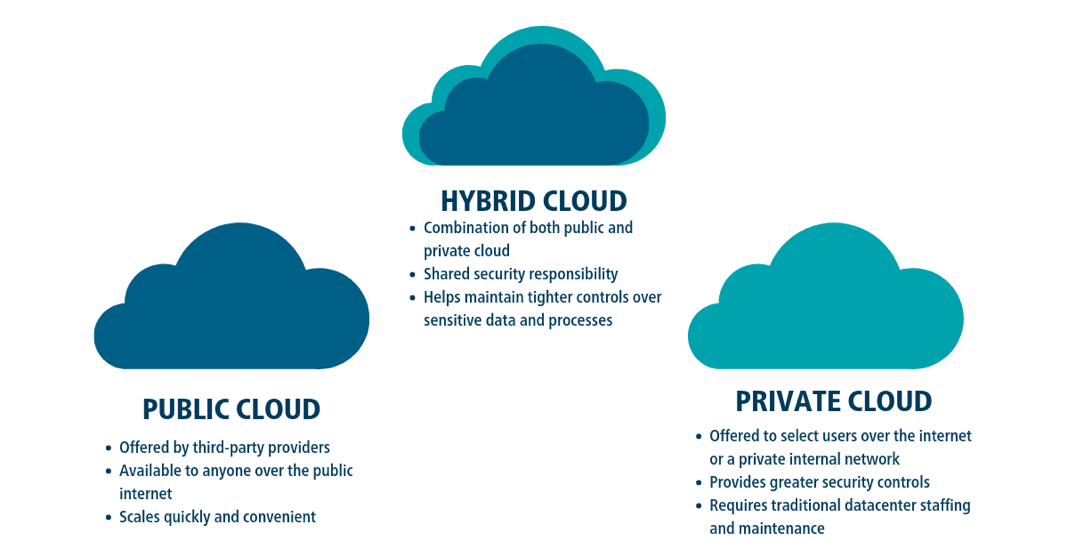
What is hybrid cloud security?
Hybrid cloud security is the process of protecting infrastructure and data tied to a company’s IT systems.
It’s referred to as hybrid cloud security because it can manage several IT systems at once, but for it to be considered a hybrid, it must include at least one private or public cloud. Companies tend to use hybrid security clouds to make flexibility, responsibility, security, and control over multiple clouds more manageable.
Although hybrid cloud security sounds more complicated than managing public or private clouds individually, they still have the same security needs around administration as well as physical and technical components:
- Administrative: Who are the people at your organisation that will be in charge of the hybrid cloud security system? What training and planning will you have in place to make sure they can keep data secure and protect against a security breach?
- Physical: What hardware is associated with your hybrid security cloud, and how will you make sure it’s safe and secure?
- Technical: What controls are in place to protect your hybrid cloud system? Will you install protections like network authentications and encryptions to protect against security breaches in your clouds?
These are just some considerations you need to be aware of when migrating to a hybrid cloud security system.
However, as more organisations look to move into a hybrid cloud environment, security is at the top of their minds. A 2018 Cloud Security Report by Cybersecurity Insiders found that 90% of cybersecurity professionals are concerned about cloud security, a figure which has increased with the growth of cloud security needs.
The main security issues in hybrid cloud computing
Issue #1: Your supply chain
The larger your hybrid cloud system is, the more likely it is that you’re using more than one tool, software, or product.
That makes it harder for all of these systems — your supply chain — to be totally secure.
If you manage your hybrid cloud yourself, this means taking a deep dive into every software and product that makes up your IT infrastructure. You’ll need to know how each vendor manages their systems, understand their source code, see if they themselves are adhering to data and regulation obligations, and when they update their security applications.
Your supply chain is just that — a chain. If one link fails, your entire IT infrastructure is at risk.
Issue #2: Your data
Data security in a private cloud is relatively straightforward as everything is secured in-house. In a hybrid cloud environment? Not so much.
That’s because when you move to a hybrid cloud, data gets intermingled between different hosting infrastructure types.
Keeping hybrid cloud data safe requires various safeguards like encryptions and network authentications. Any safeguards you put in place must also adhere to data requirements and fit into your network solutions, so they don’t compromise your supply chain.
If you implement various data security checks successfully, you can limit data exposure if your system is compromised with a security breach.
Issue #3: Your regulation compliance
Depending on the type of hybrid cloud you want to migrate to, you may have to adhere to additional regulations and compliance measures.
For example, there are highly regulated and scrutinised sectors such as government, healthcare, finance, and telecommunications that need to adhere to specific security standards. As any hybrid cloud model will likely bring additional security compliance challenges, make sure you know them and address them so you’ll continue to comply with your industry’s regulatory requirements.
How to move and secure your hybrid cloud
While there are several ways you can create and implement a hybrid cloud environment, every variation can be secured by taking the same steps.
1. Follow a rigid, consistent implementation process
Implementing a hybrid cloud requires a rigid approach, as private and public clouds each have different needs during their setups.
However, instead of creating different implementation processes for each cloud, you should always follow a single implementation process for the hybrid cloud itself. The process you follow will depend on your existing infrastructure, such as:
- Reliance on on-premise solutions
- Existing private clouds
- Use of public clouds
To tackle these issues, IBM suggests organisations apply security consistently across their entire hybrid cloud ecosystem by:
✅ Evaluating existing datasets that will be deployed to the hybrid cloud and making sure each application is using consistent encryption and authentication techniques
✅ Checking the security supply chain of each software and application that will be merged into the new hybrid cloud environment
Suppose you are moving your IT infrastructure to a hybrid environment. You may choose to keep some existing private cloud infrastructure in place to ensure the continuation of workflows while merging applications like email providers, CRM tools, and messaging apps after checking their security systems.
2. Use the right tools
Moving to a hybrid cloud is easier and safer if you are using the right tools in your tech stack.
If your tools and software already operate in clouds, you are halfway there as on-premise infrastructure is expensive to upgrade, secure and ensure you have the right skills in-house to support it. On-premise is also difficult to scale with your business, as it requires purchasing additional hardware and paying for more maintenance.
Using the right tools – like technology in your supply chain that’s secure or software that is already operating in a cloud environment – makes it easier and safer to move them into a hybrid cloud environment.
3. Have a key decision-maker
Like any operation, having a key decision-maker in charge of moving your IT infrastructure to a hybrid cloud is a smart move.
Having one person (or a steering committee) in charge makes communication easier as they will be in charge of coordination and decision-making. It can also ensure that a uniform approach to security across the hybrid cloud is being followed.
If your approach to securing your hybrid cloud isn’t unified, messages can be mixed. And after implementation, it may not be clear who is in charge of maintaining and securing the cloud.
Pro-tip: Even after moving to a hybrid cloud, the system will still have unique challenges like managing disparate environments at scale, ensuring uncompromised security, and enabling developer agility and innovation. Using a service like Redcentric, you can outsource your needs to ensure you have:
- Support for private cloud
- Support for public/community clouds
- Ability to optimise workloads across clouds
- Ability to scale & transition across clouds
- Single management across a hybrid environment
Find out more about Redcentric’s hybrid cloud solutions here.
3 Hybrid cloud security best practices
1. Hybrid cloud security is a team effort
After you move to a hybrid cloud, you must welcome your cloud service provider as a part of your team.
Choosing the right cloud service provider is an important decision. Your organisation will be trusting them to optimise workloads, enhance your system’s security, and manage clouds in a disparate environment.
This doesn’t, however, mean that you can take your foot off the pedal. Your team will still have to take a proactive approach to your hybrid cloud’s security and ensure your supply chain is only using software and applications you can trust.
For example, misconfigured data buckets can lead to security breaches, yet this responsibility is on the organisation and not the cloud service provider. When one such breach happened in 2018, exposing thousands of people’s personal details, the cloud service provider took no responsibility, leaving the organisation to salvage its public reputation.
The solution? Find a reputable cloud service provider — and work together as a team.
2. Make your process uniform across the cloud
The easier you make your security approach to understand, the less room you leave for manual error.
Making sure your team follows the same security approach across all of your systems — whether they’re using private clouds, public clouds, or on-premise infrastructure — is the best approach. Not only will it make your processes easier to follow and understand, it’ll also ensure that systems like encryptions, password protections, and authorisations are implemented across every system and strengthen them all against possible security breaches.
Suppose your administrative staff are using your system’s public clouds and on-premise infrastructure to manage customer data. You need to make sure password authentication and encryption are uniformly implemented across each system to ensure protection against data breaches.
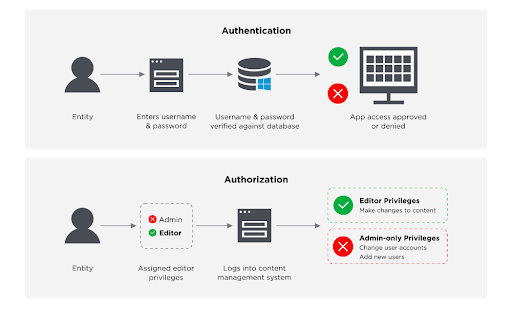
3. Adopt an IAM framework
An identity and access management (IAM) framework can keep your hybrid cloud extra secure by managing identities using software and hardware.
The framework does this by ensuring people in your organisation have the appropriate level of access to technical resources in your hybrid cloud using a mix of authentication and authorisation processes.
Implementing an IAM framework protects your hybrid cloud and its supply chain by ensuring only people with the right authorisation can access applications, databases, and infrastructure.
Imagine that your organisation regularly outsources work to contractors or freelancers, but they still need to access systems within your hybrid cloud. In that case, you can minimise the risk of a security breach by restricting their access using an IAM framework.
Interested in knowing more about how your organisation can benefit from hybrid cloud security? Redcentric provides managed hybrid cloud services, which gives organisations the power to innovate anywhere while operating seamlessly and securely. Learn more here.