Infrastructure-as-a-Service (IaaS) provides the ability to run many customer servers on the same physical server hardware through the use of server virtualisation. The concept is a repeat of the technology being used with local and wide area network virtualisation using VLANs and MPLS. These are both widely used and accepted technologies that are viewed as secure by many security standards.
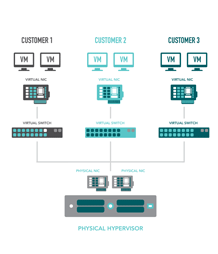
 The server virtualisation process creates multiple virtual servers that run on top of the underlying physical server. The software that performs this task – the hypervisor – is tasked with scheduling the many virtual servers’ access to the physical resources. Each virtual server is largely unaware that it is running alongside other virtual servers as it can only see its own virtual hardware – it has no access to the processor, memory or disk storage of the other virtual servers. This inherent separation of virtual servers allows IaaS providers to run many customers alongside each other on the same physical hardware.
The server virtualisation process creates multiple virtual servers that run on top of the underlying physical server. The software that performs this task – the hypervisor – is tasked with scheduling the many virtual servers’ access to the physical resources. Each virtual server is largely unaware that it is running alongside other virtual servers as it can only see its own virtual hardware – it has no access to the processor, memory or disk storage of the other virtual servers. This inherent separation of virtual servers allows IaaS providers to run many customers alongside each other on the same physical hardware.
This type of shared IaaS arrangement is a perfect option for customers starting out with server hosting and looking to avoid large capital expenditure. It allows customers to use a share of the existing platform, in other words your server is one of many using the same underlying hardware such as CPU, memory, and storage. The upside is that this spreads out the cost of hardware, bandwidth and maintenance among all hosted clients.
One might assume that there has to be a trade-off in such a scenario, and that users have to accept a lesser performance in return for reduced costs. That shouldn’t be taken as a given, as it’s very much a case of how the IaaS cloud solutions provider operates – the professional, client-centric supplier will ensure that any shared hosting provision is absolutely fit for purpose, and that affordability doesn’t come at the price of operability.
The priority has to be helping customers get the best hosting fit, and while for many shared hosting will remain the optimum solution, we also recognise companies grow and consequently outgrow their current resource allocation. The key is making the necessary transition swift and painless, and one of the virtues of IaaS is that its elasticity enables providers to switch customers out of a shared platform and onto a tailored, dedicated platform quite seamlessly and effortlessly.
If safeguarding performance is one core aspect of IaaS provision, then addressing security is another. The quality of security is the same whether a customer is on shared or dedicated hosting, but we accept there can often be greater sensitivity around the notion of a shared environment. Can shared ever equate to safe? Always, and there’s a useful analogy that we can use to illustrate just why that is so.
A shared environment is like living in a block of apartments shared with other residents. Every tenant uses the common resources like the car park, reception and lifts (the memory, storage and CPU of the underlying hardware) and yet maintains the privacy of their own apartment (the virtual machine). The whole block is comprehensively protected with gated parking, key coded front entrance, card-operated lift, CCTV, security guards, concierge or caretaker and that’s before you get to your own front door, which has a spy hole, locks and bolts, and an alarm. (firewalls, ports, intrusion detection, prevention devices, full-time monitoring).
There are virtual servers connected by virtual network cards to virtual networks and these virtual networks can be protected by virtual firewalls. The virtual firewalls might be virtualised instances of traditional physical network firewalls, or they may be special instantiations of network traffic control mechanisms that are integrated with the hypervisor environment. Either way, they offer very real protection.
Making the switch from shared to dedicated is invariably a strategic decision – forecasts indicate that at some point the customer in question will outgrow its current allocation of shared resources? If it does, then best to make provision for a move to a dedicated IaaS platform – but the beauty of IaaS is that the work to make that change happen is all done by the provider at the back end, without any complications at the front end. The same security safeguards will still be in place, it will all look and feel the same, indeed the only thing to change will be the underlying resources – they are now yours and yours alone, and they are essentially infinite in their capacity.
IaaS offers both a way into, and a long-term route through, the world of agile, streamlined hosted infrastructure, thanks to its shared and dedicated options. Most importantly, there is no need to compromise – you can always have the optimum solution for your given situation.




